Everybody,
I've created an app that allows users to protect their NAS by only allowing hosts that they allow.
Right now security is a really big threat for our data, because all these apps and services that we open to the internet can have vulerabilities at some point...and we cannot close all the vulnerabilities.
And even when there are no vulnerabilities, hackers will try to bruteforce our usernames and passwords for all those services and applications...
That's why whitelisting is the best solution, you block everyone out except the servers(like backup servers) or friends that you trust.
I've created this app because the default app lacks some features.
This app extends the whitelist functionality of QNAP by adding:
- A remote available interface for managing your whitelist
- Supporting DNS entries (for allowing access to your clients on the road by identifing them based on their dyndns host or your backup server hostname or even your uptimerobot hostnames,etc...)
- Enforce the idea of not forgetting to include your private networks so that you don't lock out yourself(but if you do, whitelisting can be disabled by pressing your reset button for 1,5 seconds (soft reset))
- Ability to add hosts in an automated way for temporary access untill the pre-defined time has expired (tickets)
- optional two-factor authentication (trust a server on the internet, that server can grant permissions to your home nas-> so in order to attack your nas , first they need to authenticate themselfs on your trusted server)
Although enabling country blocks seems the best thing to do, we discourage the usage of so many IP's althoug it is much better then having the whole internet accessing your nas
We recommend to use the two-factor authentication script, that way you keep the scope of computers conencting to your nas very small.
See screenshot
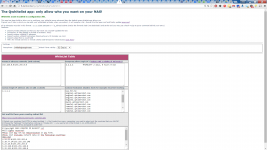
Version 1.6:
http://www.positiv-it.fr/QNAP/APP/Qwhitelist_1.150914.qpkg.zip
1) unzip
2) Install
3) Execute
I've created an app that allows users to protect their NAS by only allowing hosts that they allow.
Right now security is a really big threat for our data, because all these apps and services that we open to the internet can have vulerabilities at some point...and we cannot close all the vulnerabilities.
And even when there are no vulnerabilities, hackers will try to bruteforce our usernames and passwords for all those services and applications...
That's why whitelisting is the best solution, you block everyone out except the servers(like backup servers) or friends that you trust.
I've created this app because the default app lacks some features.
This app extends the whitelist functionality of QNAP by adding:
- A remote available interface for managing your whitelist
- Supporting DNS entries (for allowing access to your clients on the road by identifing them based on their dyndns host or your backup server hostname or even your uptimerobot hostnames,etc...)
- Enforce the idea of not forgetting to include your private networks so that you don't lock out yourself(but if you do, whitelisting can be disabled by pressing your reset button for 1,5 seconds (soft reset))
- Ability to add hosts in an automated way for temporary access untill the pre-defined time has expired (tickets)
- optional two-factor authentication (trust a server on the internet, that server can grant permissions to your home nas-> so in order to attack your nas , first they need to authenticate themselfs on your trusted server)
Although enabling country blocks seems the best thing to do, we discourage the usage of so many IP's althoug it is much better then having the whole internet accessing your nas
We recommend to use the two-factor authentication script, that way you keep the scope of computers conencting to your nas very small.
See screenshot

Version 1.6:
http://www.positiv-it.fr/QNAP/APP/Qwhitelist_1.150914.qpkg.zip
1) unzip
2) Install
3) Execute

